
Document fraud detection with OpenCV in Python: real tests and limitations.
Comparatives
Dernière mise à jour :
January 23, 2026
5 minutes
Invoice fraud is often perceived as a marginal or exceptional risk. In reality, it is one of the most common sources of financial loss for organizations of all sizes. Fake invoices, supplier impersonation, payment diversion, and subtle manipulation of approval processes continue to bypass traditional controls. While some cases are caused by simple billing errors, invoice fraud is intentional by nature. It relies on small inconsistencies, operational pressure, and trust in documents that appear legitimate. Understanding how invoice fraud works is the first step toward detecting it before payment.
How invoice fraud works, the most common red flags, and why basic controls are no longer enough.
Invoice fraud refers to deliberate actions aimed at obtaining unauthorized payments through the invoicing process. This may involve issuing invoices for services that were never delivered, impersonating legitimate suppliers, or diverting payments to fraudulent bank accounts.
What makes invoice fraud particularly effective is its ability to mimic normal business activity. Fraudsters reuse familiar formats, realistic templates, and standard wording. As invoice volumes grow, individual anomalies become harder to detect, allowing fraudulent invoices to pass unnoticed.
Invoice fraud rarely relies on a single obvious mistake. In most cases, it emerges from the accumulation of small warning signs. A missing reference, an unusual amount, or an unexpected supplier detail may seem harmless in isolation. Taken together, however, these inconsistencies often reveal patterns that deserve closer attention. Effective detection depends on recognizing how red flags interact over time rather than treating each invoice as an isolated document.
Supplier-related fraud is one of the most common entry points for invoice fraud. In some cases, the supplier does not exist at all. In others, fraudsters reuse the identity of real companies to issue fraudulent invoices. These invoices often look credible. Company names, addresses, and layouts appear legitimate, making fraud difficult to spot without checking supplier history, consistency, and payment details. Even well-formatted documents can be misleading, which is why relying solely on invoice appearance is no longer sufficient.
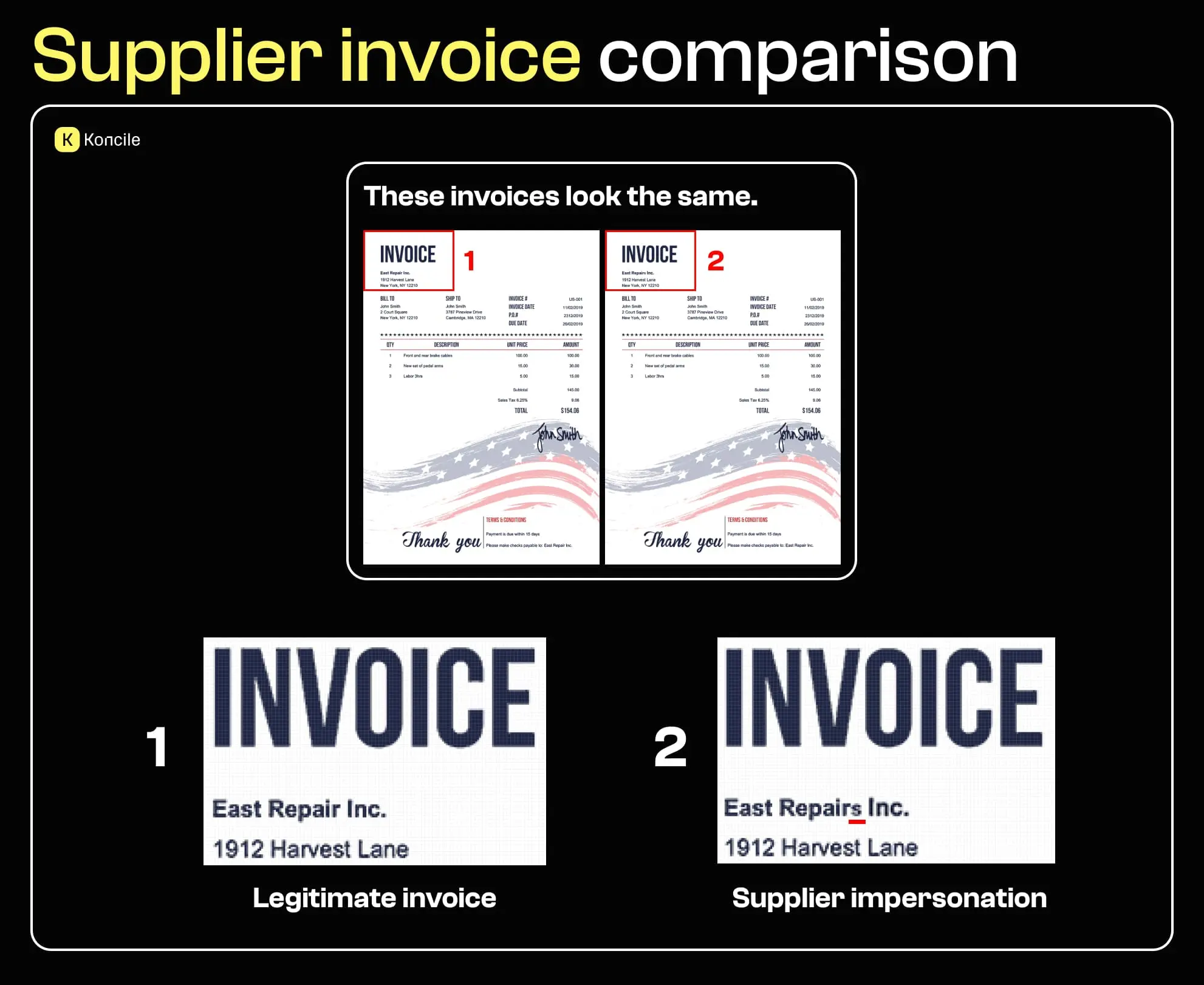
We know the second invoice is fraudulent only because we know the supplier’s real name and notice the added ‘s’.
Many invoice fraud schemes do not start with fake documents but with compromised communications. Through phishing or credential theft, attackers gain access to real email exchanges between suppliers and finance teams. Once inside an existing thread, fraudsters can introduce fraudulent invoices, replace attachments, or request urgent payment changes. Because the context feels authentic, these attacks frequently bypass visual and procedural checks.
Payment diversion is one of the most financially damaging forms of invoice fraud. The invoice itself may appear legitimate, but the bank details have been altered to redirect funds to a fraudulent account. Mismatched account holder names, unexplained foreign bank accounts, or sudden changes in payment instructions are common warning signs. In practice, detecting these inconsistencies often requires comparing invoice data with historical payment information or external records, such as those obtained through bank statement extraction.
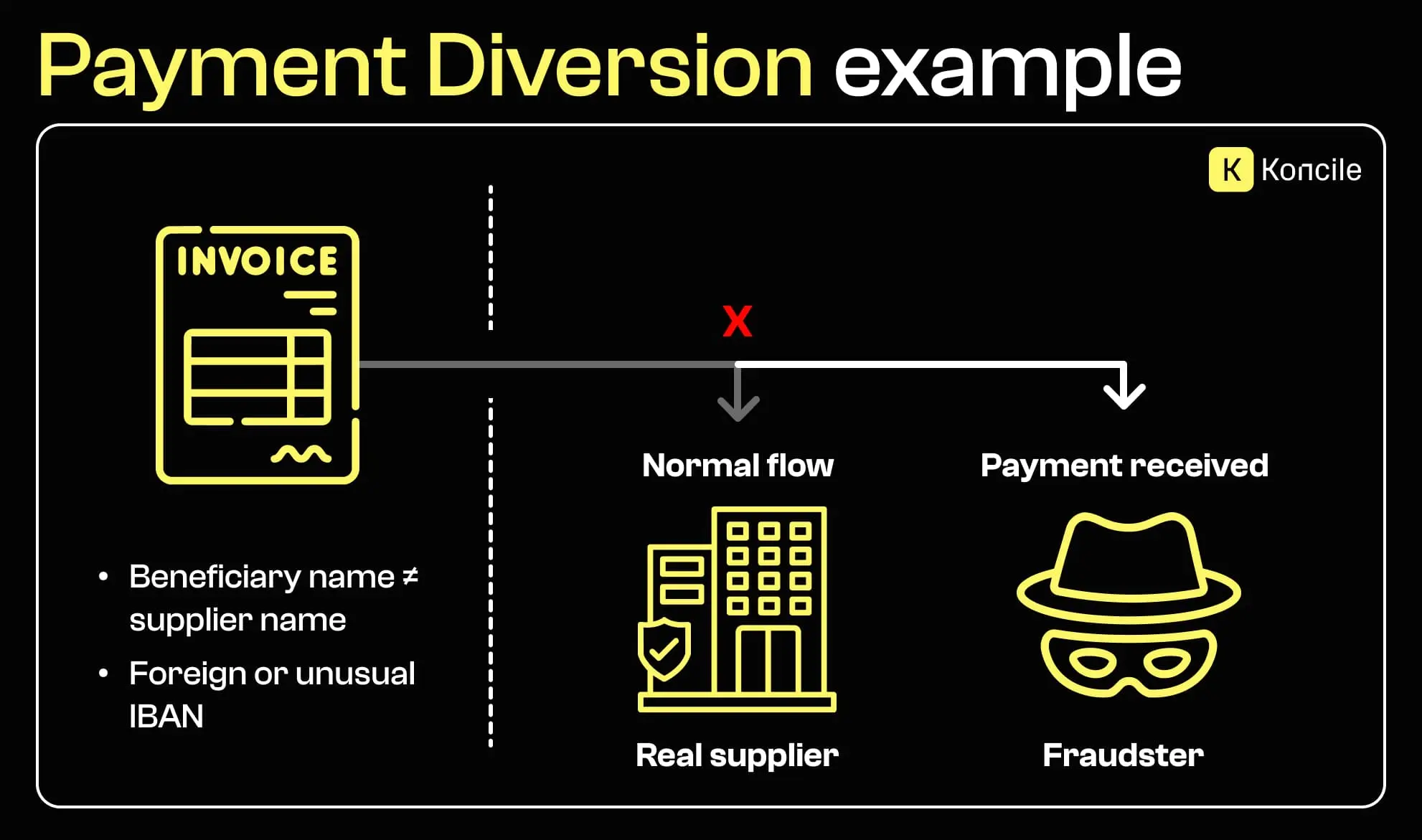
Fraudulent invoices often rely on ambiguity. Missing invoice numbers, unclear dates, or incomplete seller information make verification more difficult and reduce traceability. In some cases, inconsistencies are intentional. An invoice with unusual formatting or irregular numbering may be designed to blend into high volumes of documents without attracting attention.
Vague descriptions are a recurring characteristic of fake invoices. Terms such as “services rendered” or “consulting fees” without further detail make it difficult to confirm whether work actually took place. The absence of deliverables, time periods, or contractual references limits internal verification and allows fraudulent invoices to remain unchallenged. This is particularly problematic when invoices are processed at scale, where structure and data consistency matter more than visual presentation, as highlighted in many Invoice OCR use cases.
Fraudsters are often aware of internal approval thresholds. To avoid additional scrutiny, invoices are issued just below validation limits or repeated at similar “safe” amounts. Individually, these invoices may not raise concerns. Over time, however, repeated patterns can lead to significant financial losses.
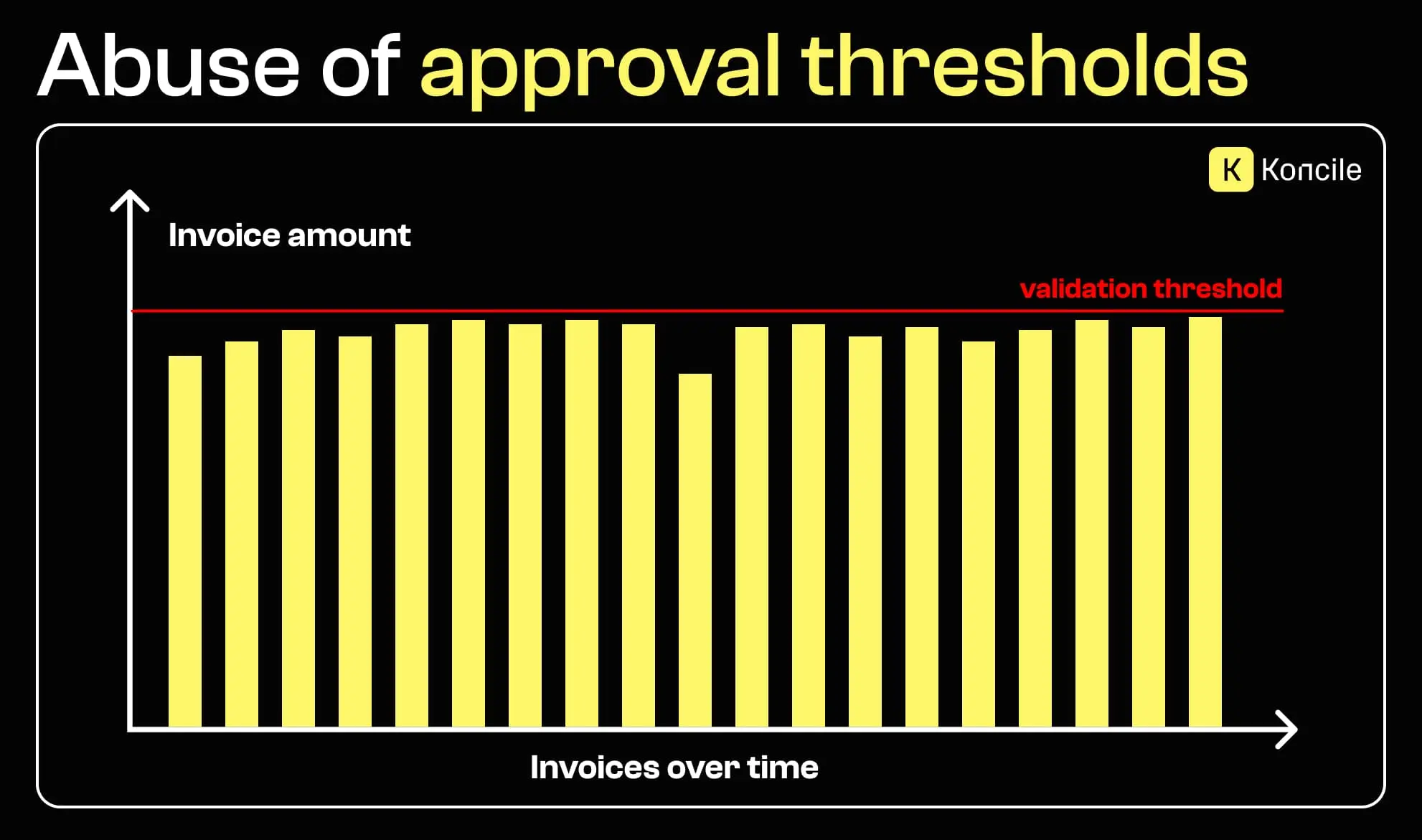
Each invoice looks acceptable. The fraud only appears when invoices are viewed together.
Invoice fraud is not always external. In some cases, internal actors contribute directly or indirectly by approving invoices without proper verification or bypassing established controls. Weak segregation of duties and overreliance on trust increase exposure to this type of fraud, especially in high-volume environments.
A professional layout, recognizable logo, and structured format do not guarantee legitimacy. Modern fraudulent invoices often use realistic templates and branding that closely resemble genuine documents. Visual inspection alone is no longer a reliable safeguard. Detecting invoice fraud requires consistency checks across multiple data points rather than trust in document appearance.
Invoice fraud rarely begins with a large anomaly. More often, it develops gradually. Amounts increase slowly, billing frequency changes, or services expand without formal validation. When invoices are reviewed individually, these trends remain invisible. Patterns only emerge when documents are analyzed collectively over time, using approaches similar to those described in intelligent document processing.
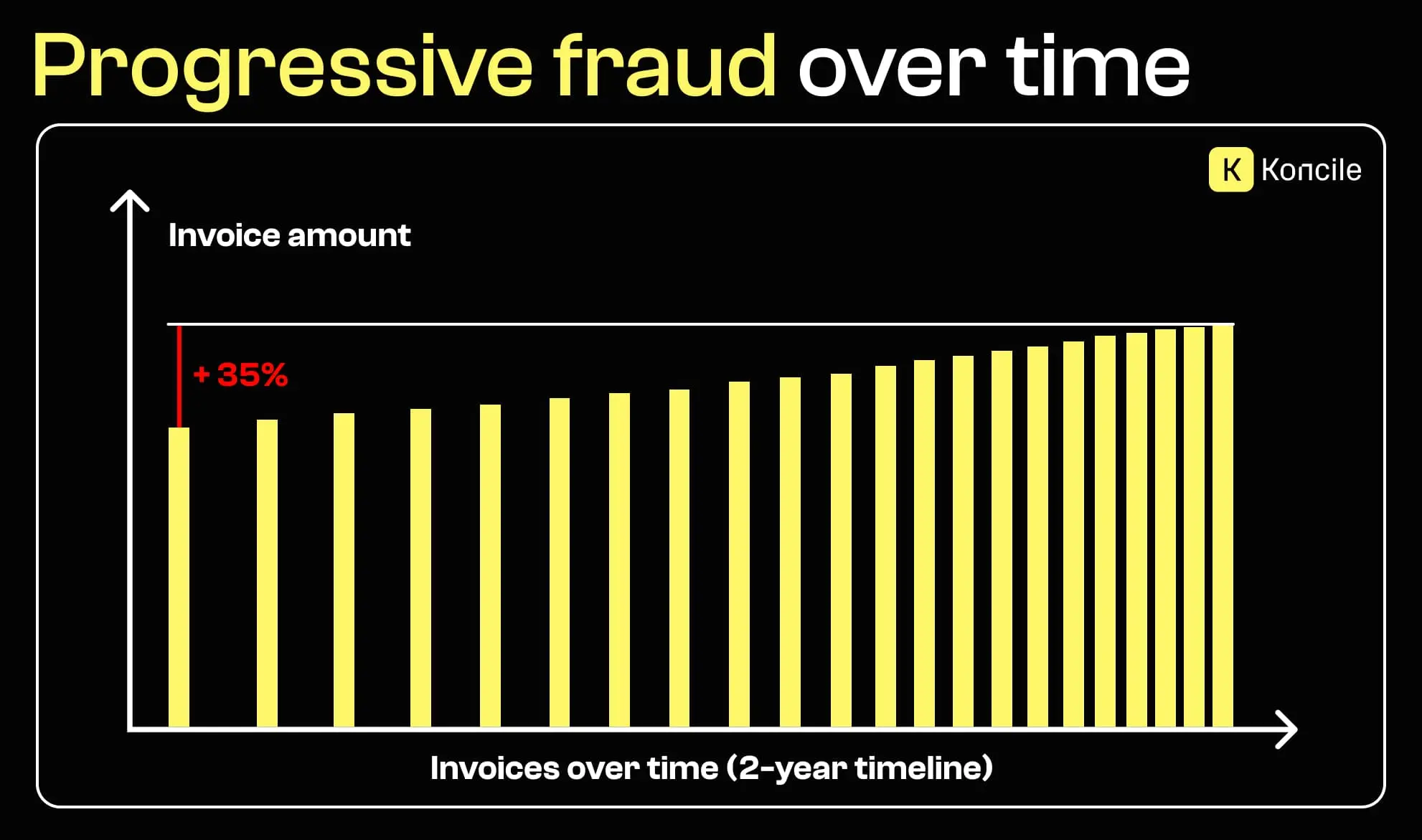
Manual controls struggle to scale as invoice volumes grow. Operational pressure, repetitive tasks, and time constraints reduce the effectiveness of human review. Fraudsters exploit this reality by blending into routine workflows. Over time, isolated checks become insufficient to detect coordinated or evolving fraud schemes.
Detecting invoice fraud requires more than reviewing documents one by one. Effective controls depend on cross-checking invoices against suppliers, contracts, payments, and historical behavior. Moving toward structured document fraud detection allows organizations to identify inconsistencies that remain invisible at the individual invoice level and significantly reduces exposure to complex fraud patterns.
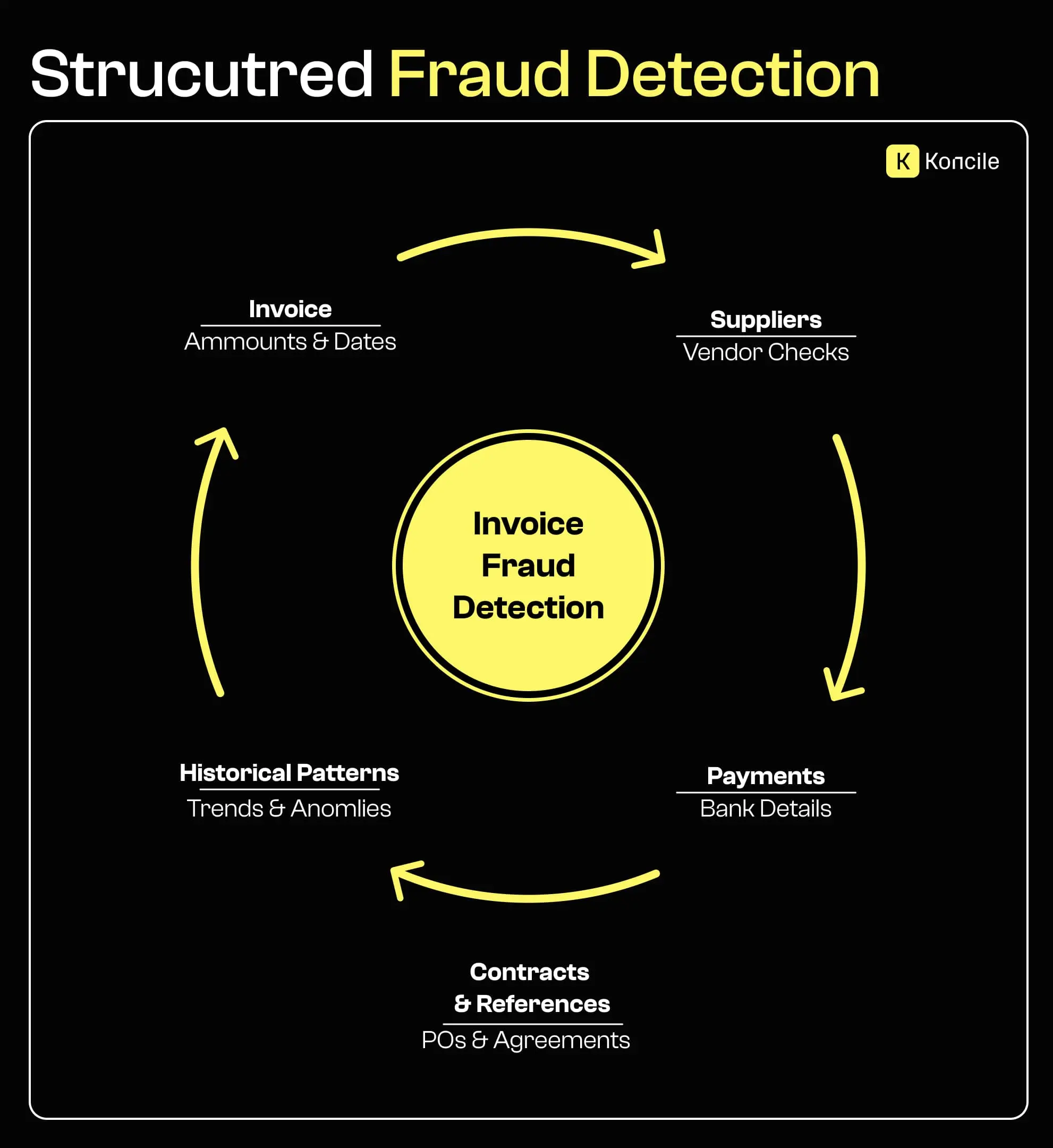
The impact of invoice fraud extends beyond direct financial losses. Investigations consume time, audits disrupt operations, and disputes strain supplier relationships. Repeated incidents erode trust in financial processes and increase operational friction, making fraud prevention a matter of long-term organizational resilience.
Invoice fraud rarely relies on a single obvious error. It is built on a combination of small signals, operational pressure, and misplaced trust in documents that appear legitimate. As invoice volumes grow and fraud techniques evolve, organizations must move from reactive checks to structured, consistent detection approaches to limit risk before payment occurs.
Move to document automation
With Koncile, automate your extractions, reduce errors and optimize your productivity in a few clicks thanks to AI OCR.
Resources

Document fraud detection with OpenCV in Python: real tests and limitations.
Comparatives

Comparative test of Open Source OCR API tools in 2026: integration difficulty, JSON output quality, self-hosting and real-world benchmark.
Comparatives

Yann LeCun’s vision for the future of AI, beyond LLMs and AGI.
Comparatives